

Vishal Kotalwar
5 Minutes read
The Next Generation Firewall To Protect Your Enterprise Network Resources
Firewall is an integral and important part of every networking infrastructure as a firewall at the perimeter of the network is network’s first line of defence against attacks aimed at breaking it. Firewalls have been around for decades filtering traffic based on IP addresses, ports and protocols.
These are traditional firewalls, taking decisions based on ports, protocols and IP addresses or for that matter, based on state of the connection. In today’s world, it is neither sufficient nor reliable to implement firewall policies in such a inflexible way. Network attacks have grown more in sophistication and intensity. Attackers are always trying to exploit weakness and loop holes in security policies or OSes running on devices to gain un-authorized access or/and steal information. Firewalls need more context of the network that they are protecting to make better decisions in an intelligent way.
Next Generation Firewall (NGFW) is the next version of firewalls which adds more intelligence to the decision making by getting information from packet payloads. The technology is called Deep Packet Inspection.
Some of the important features of NGFW are:
- Signature-based intrusion detection/prevention system (IDS/IPS)
- Application identification or Application Visibility & Control (AVC)
- Full stack visibility
- White listing or black listing of Applications/URLs
- Upgrade path to include future security threats and information feeds
An Intrusion Detection/Prevention System (IDS/IPS) is a network security / threat detection / prevention technology that examines network traffic flows to detect and prevent vulnerability exploits. Vulnerability exploits usually are in the form of malicious inputs to a target application or service (like attachment in a mail or disguised executable) that attackers use to gain control of an application or machine.
The IPS uses a signature-based detection mechanism to detect exploits. Signature-based detection primarily depends on a set of uniquely identifiable data patterns (or signatures) in each exploit. These patterns are matched with a database of rules to identify the exploit and then take necessary action.
Intrusion Detection System (IDS) unlike IPS will only alert the administrator if it encounters a threat. IDS cannot drop a packet if it matches any malicious activity.
IDS/IPS signature based rule:
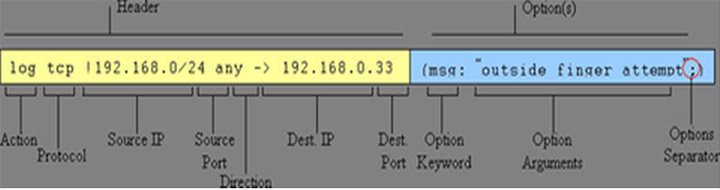
Sample rule:
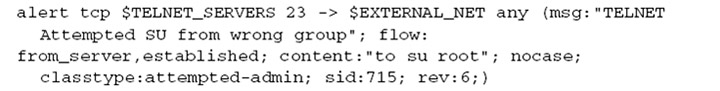
Pattern matching is the most crucial part of any IDS/IPS system. Generally, signatures have one more more patterns. Of each signature, one prominent pattern is used by the multi-pattern-matcher for comparison. That way the program can exclude many signatures from being examined, because a signature can only match when all its patterns match and these comparisons are CPU heavy operations. Hence performance of pattern matcher will determine the overall performance and throughput of the system so a compact, optimized and fast pattern matcher is desirable for a given IDPS.
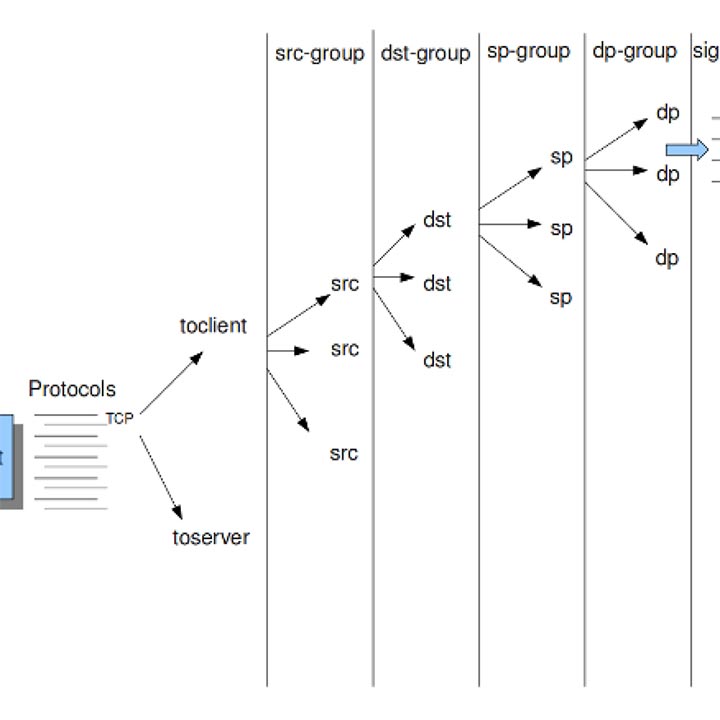
Internet service providers and Network administrators need to understand which application traffic is flowing through their networks, which applications are consuming most bandwidth and whether customer preferred applications are given priority. This helps them in managing their networks to the optimum. Previously, this knowledge was gathered by classifying flows by their IP addresses, port numbers, DSCP markings (assuming that the operator has classified applications based on DSCP markings), and application names using NBAR, among other techniques. Most of these techniques were heavily dependent on port numbers used for communication but with changing needs and technologies; this dependency is making classification impossible. A look at packet payload using Deep Packet Inspection (DPI) is required to correctly classify the application from the underlying protocol. For example many cloud based services and applications are delivered over HTTP and HTTPS which use same ports for web traffic such as Netflix, WebEx, YouTube etc.
Only initial few packet are required for any identifier to identify an application. Identifier has pre defined application signatures and matches incoming packet payloads with these signatures to determine which application the conversation belongs too. Again here, pattern matching will determine the performance. Once applications are identified, they can be used for numerous purposes like application firewall, application QoS, subscriber analytics etc.
Many argue that Web firewalls are part of NGFW or they are type of NGFW with specific use case. That debate is for another day but Web Application Firewalls (WAF) are aimed at protecting web servers and hosted web applications against attacks in the application layer via HTTP(S) and against non-volumetric attacks in the network layer.
NGFW CHALLENGES:
Movement of network functions to cloud is another big challenge for NGFWs. Most common deployment of NGFW is at the perimeter of enterprise network (though I strongly believe that a separate instance of NGFW should protect critical parts of enterprise network like data centers, web servers individually with more function specific focused rules). With cloud, the concept of network perimeters is vanishing and traditionally NGFWs have been designed with proprietary hardware boxes not suitable for cloud. Though most of the commercial vendors have virtualized versions of their NGFW offerings, the adaptation by industry has been slow.
NGFWs rely on DPI technology for its functionality and encrypted traffic (both SSL & IPSec) throws challenges to DPI and in-turn to NGFWs. Most of the commercial NGFWs have SSL decryption functionality for decryption before performing DPI operations. This has its own problems but there is some solution to encrypted traffic problem.
Related Insights




Top 5 Hard Truths About Your Governance Strategy

ETL Simplified: Storing and Transforming Data Fully Inside Databricks

