
ACL Digital
DevSecOps for Cloud-Native Applications: Strategies and Best Practices
The evolution of cloud-native applications has revolutionized how we design, develop, and deploy software. As organizations strive to innovate and scale rapidly, the need for robust security practices embedded within the development lifecycle has never been more critical. Enter DevSecOps—a paradigm that integrates security into every phase of the DevOps pipeline, ensuring that security is not an afterthought but a foundational component of the development process.
DevSecOps aims to fill up the gap between development, operations, and security teams, nurturing a culture of collaboration and shared responsibility. This approach is especially pertinent for cloud-native applications, which leverage the scalability, flexibility, and resilience of cloud computing. By incorporating security practices from the outset, organizations can protect their cloud-native environments against a myriad of evolving threats, ensuring their applications remain secure, compliant, and performant.
What are Cloud-Native Applications?
Cloud-native applications are software programs designed and built specifically to leverage the advantages of cloud computing frameworks. Unlike traditional applications that may have been developed for on-premises infrastructure and later migrated to the cloud, cloud-native applications are natively architected for the cloud from the ground up. This intrinsic design approach allows these applications to fully exploit the scalability, flexibility, and distributed nature of cloud environments.
Cloud-native applications are typically composed of microservices, which are independently deployable services that work together to form a larger application. These applications are often deployed in containers, managed by orchestration tools like Kubernetes, to ensure efficient resource usage and seamless scaling. By harnessing the capabilities of cloud platforms, cloud-native applications can achieve high availability, rapid deployment, and dynamic scalability, making them ideal for modern business needs that demand agility and resilience.
What are the Characteristics of Cloud-Native Applications?
Cloud-native applications embody a modern approach to software development tailored for the cloud environment. Central to their architecture is the use of microservices—a design pattern where applications are composed of small, independently deployable services. These services communicate via APIs and operate within containers, which encapsulate their runtime environment and dependencies. This containerization ensures consistency across different computing environments, from development to production, and facilitates efficient scaling and management through orchestration tools like Kubernetes.
What are the Characteristics of Cloud-Native Applications?
Generative AI is a branch of artificial intelligence that creates new content like text, images, sound, and code. It learns from large datasets to produce new content. The GPT series, including GPT-3 and GPT-4, is famous for its proficiency in language tasks.
Generative AI has diverse applications, from generating creative content to automating repetitive tasks, and it is finding new roles in areas like disaster recovery, finance, and DevOps.
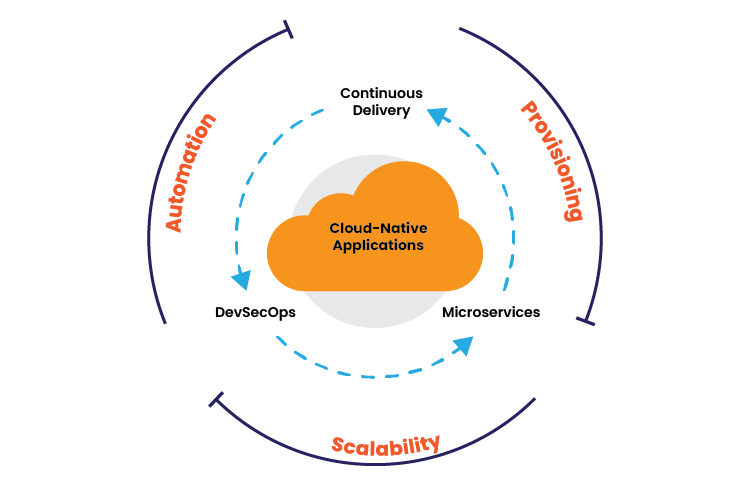
Moreover, cloud-native applications embrace DevOps practices, integrating development (Dev) and operations (Ops) teams to streamline processes like continuous integration and continuous deployment (CI/CD). This approach will automate testing, integration, and deployment workflows, fostering a culture of collaboration and enabling rapid delivery of features and updates.
Automation is further reinforced by Infrastructure as Code (IaC), where infrastructure components are defined and managed through machine-readable scripts. This ensures consistency, reduces manual errors, and accelerates provisioning and configuration tasks, thereby enhancing the application’s scalability and operational efficiency. Together, these characteristics—microservices architecture, containerization, DevOps practices, and automation—define cloud-native applications as versatile, scalable, and resilient solutions optimized for the dynamic demands of modern cloud environments.
- Microservices Architecture
- Containerization
- Dynamic Orchestration
- API-First Design
- DevOps Practices
- Elastic Scalability
- Resilience and Fault Tolerance
- Automation and Infrastructure as Code (IaC)
- Observability and Monitoring
The Need for DevSecOps in Cloud-Native Environments
In cloud-native environments, the need for DevSecOps integrating security practices early and continuously throughout the software development life cycle is paramount due to several key factors.
Cloud-native applications leverage dynamic and scalable infrastructure provided by cloud platforms. This flexibility introduces new attack vectors and security challenges that traditional security measures may not adequately address. Without proactive security measures embedded into every stage of development and deployment, these applications are vulnerable to cyber threats, data breaches, and compliance risks.
The modular nature of cloud-native applications, often built on microservices architecture and deployed in containers orchestrated by tools like Kubernetes, increases the complexity of security management. Each microservice and container represents a potential entry point for attackers if not properly secured. DevSecOps practices ensure that security considerations, such as vulnerability assessments, secure coding practices, and identity management, are integrated into the development process from the outset. This approach not only mitigates risks but also promotes a proactive security posture that adapts to the evolving threat landscape.
The rapid pace of development and deployment in cloud-native environments necessitates automated security testing and monitoring. DevSecOps facilitates continuous security testing (as part of CI/CD pipelines) and real-time monitoring of application performance and security metrics. This proactive approach enables teams to identify and remediate vulnerabilities and threats swiftly, minimizing potential impact on operations and maintaining compliance with regulatory requirements.
Ultimately, adopting DevSecOps in cloud-native environments is essential for organizations aiming to achieve robust security, maintain operational resilience, and build trust with customers and stakeholders. By integrating security into the DevOps workflow, teams can effectively manage risks while accelerating innovation and ensuring the stability and integrity of cloud-native applications throughout their lifecycle.
Best Practices for Implementing DevSecOps in Cloud-Native Applications
Implementing DevSecOps in cloud-native applications involves adopting several key strategies and best practices to ensure robust security throughout the development lifecycle. Here are some essential approaches:
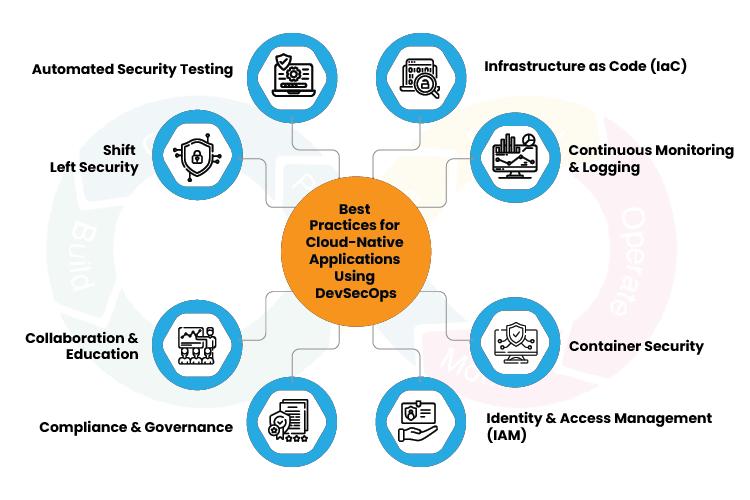
Shift Left Security
Begin security activities as early as possible in the development process. This includes integrating security checks into the CI/CD pipeline to identify and address vulnerabilities in code, dependencies, and configurations during development and before deployment.
Automated Security Testing
Implement automated security testing tools and practices such as static application security testing (SAST), dynamic application security testing (DAST), and software composition analysis (SCA). These tools help detect and mitigate security issues continuously, ensuring that vulnerabilities are identified and remediated promptly.
Infrastructure as Code (IaC) Security
Utilize IaC principles to define and manage infrastructure configurations through code. Implement security best practices, such as least privilege access, secure storage of credentials, and automated validation of configurations, to ensure consistent and secure deployment of infrastructure components.
Continuous Monitoring and Logging
Establish robust monitoring and logging mechanisms to track application behavior, detect anomalies, and respond to security incidents in real-time. Implement centralized logging and monitoring solutions to aggregate and analyze logs across microservices and containers.
Container Security
Secure container images by scanning them for vulnerabilities before deployment. Implement runtime security measures, such as container network policies and runtime anomaly detection, to protect against container-based attacks and ensure isolation and integrity.
Identity and Access Management (IAM)
Implement strong IAM practices to manage identities, roles, and permissions across cloud-native applications. Utilize identity federation, multi-factor authentication (MFA), and least privilege access controls to minimize the risk of unauthorized access.
Compliance and Governance
Implement policies, procedures, and automated checks to ensure compliance with regulatory requirements and industry standards. Regularly audit and assess security controls to maintain compliance and mitigate legal and reputational risks.
Collaboration and Education
Foster a culture of security across development, operations, and security teams through collaboration, training, and shared responsibility. Encourage continuous learning and awareness of emerging security threats and best practices within the organization.
By implementing these strategies and best practices, organizations can effectively integrate security into the DevOps workflow for cloud-native applications. This proactive approach not only enhances the overall security posture but also enables teams to innovate rapidly while maintaining the confidentiality, integrity, and availability of their cloud-native environments.
As cloud-native applications continue to drive innovation and operational efficiency, the integration of security practices through DevSecOps becomes essential. By embedding security into every phase of the development lifecycle, organizations can proactively address vulnerabilities, ensure compliance, and enhance the overall resilience of their applications. The shift-left approach, coupled with automated security testing, robust monitoring, and strong identity management, enables teams to detect and mitigate threats early and continuously.
Staying ahead of the curve is essential for any enterprise looking to thrive in today’s fast-paced digital landscape. At ACL Digital, we empower businesses to harness the power of technology and drive transformative growth. Our comprehensive suite of services is designed to address your unique challenges and propel your enterprise towards success. At ACL Digital, we empower businesses to harness the power of technology and drive transformative growth. Our comprehensive suite of services is designed to address your unique challenges and propel your enterprise towards success. Reach out to our team at business@acldigital.com for more details.
