

ACL Digital
6 Minutes read
Addressing Public Cloud Security Challenges through Automation
Cloud security loopholes often make news one way or the other. Frequently, they are stated with imprecise explanations. The uncertainty may seem intimidating when it comes to cloud computing and securing public cloud services. But it is not so. You just need to manage cloud resources efficiently via adaptable and unified cloud security solutions. Tackling public cloud security challenges is not so difficult. All you need to do is seek the expert help of cybersecurity professionals who can untangle the complications of protecting the unexpected workloads in vigorous and faster environs.
If you are looking for proven expertise to handle the rise of net new public cloud security challenges, then look no further than ACL Digital. The company comprises experienced software engineers who can easily deliver Cloud-based SASE solution for Next-Gen firewall, SSL inspection, IPsec VPN and Cloud Brokerage in a unified framework model. We are well-equipped to handle the day-to-day operational hassles especially for companies and individuals who possess a huge number of assets and no efficient way to track or supervise them.
In this blog, we would like to focus on and emphasize some of the top public cloud security challenges faced by the industry and the most important conditions essential for solving those issues through automation.
Legacy Security Solutions have Restricted Functionality
Legacy data warehouse tools are very expensive and will not make the required cut. Many times, people do tend to port in an inefficient architecture into the public cloud. As many applications have started moving to the cloud, the stack configured in the datacenter is unable to manage the varying traffic patterns.
Using conventional network security tools would have been ideal when applications were hosted in more static and centralized data centers. Presently, these tools are not designed for dynamic virtual environments. To tackle public cloud security challenges and maintain security and compliance visibility, security professionals would like to have the ability to:
- Find their assets
- List and inventory the assets
- Evaluate the assets regularly to keep a check on threats
- Provide verification and monitor the whole process
Cloud Infrastructure Modifications are Too Quick and Tools Cannot Keep Up
You cannot keep up with the speed of change if you are not having the right tools developed keeping the cloud infrastructure in mind. At times, you might lose visibility into the infrastructure facility if things are moving very quickly.
If the compliance and security stakeholders are not aware of how the network infrastructure is configured, then there is a disaster waiting to happen, as the assets can have major vulnerabilities. E.g., Facebook and Capital One had reported compromise of their S3 environment. This kind of issue comes to the fore primarily due to being unaware of the presence of the asset and not knowing that it is misconfigured, which poses a very big problem.
Also, when you move into a complex environment that contains microservices, especially Kubernetes and Mesos in containers, it may vanish after a very brief period (usually in seconds) just by completing a very small job. In this kind of environment where you do not have uninterrupted visibility, there is no other way to manage than lean towards automation.
While uninterrupted visibility is just one part of the equation, you will also require automated tracking and notification of remediations which is very vital to solving public cloud security challenges. Priorly, remediation was a very slow process, and the right owners should have a strong understanding of the level of priority and urgency on their conditions.
Nowadays with cloud environments being in continuous motion, remediation data stream must be continuous and should be in the desired form for your Ops team to make it highly active and beneficial.
Duplicating Network Perimeter Strategy
The traditional data center had relatively fewer components and was more identical, whereas modern applications are cloud-based environments and have more components and are more varied. Furthermore, in most cases, the perimeter orientation tends to create more security challenges even though there are perimeter controls.
Normally, when you take a traditional data center environment and introduce private cloud infrastructure, you are most likely to add containerization because of multiple virtualization environments. In this type of situation, you are most likely to introduce automation tools in the data center. Here the basic security model even though it is perimeter-driven remains very much the same.
Adding public cloud infrastructure is a giant leap for many organizations because of the shared responsibility model. It is ideal for appropriate compliance and security as it will not have to deal with a lot of components in the datacenter. Here, the new public cloud security must be dealt with a new method to security, such as safeguarding and monitoring the configuration of the environments.
So, what are the key features that you should look to enable these facilities?
While automation is crucial in safeguarding your public cloud infrastructure, your standard cloud security visibility solution should have the following attributes to back it:
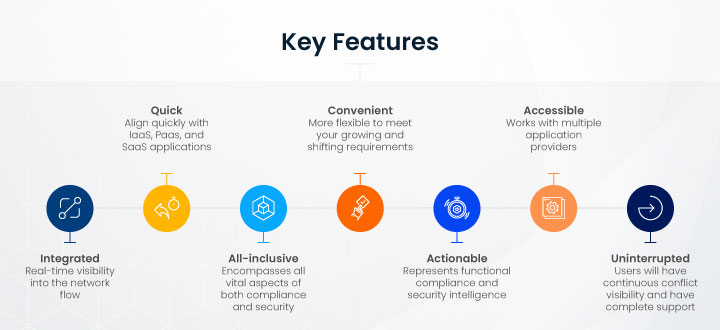
Why automation is a must to face unexpected public cloud challenges?
If you do not have continuous insight into the dynamic public cloud environments, it is almost impossible to control the security position or to handle the public cloud security challenges. As uninterrupted detection, inventory, and assessment is crucial, efficient automation of these needs in a dynamic Software as a Service (SaaS), Platform as a Service (PaaS), Infrastructure as a Service (IaaS) environment is a must.
Effective automation reduces the duty of manual monitoring present in legacy systems. It also significantly simplifies the management of SaaS, PaaS, and IaaS that allows your organization to alleviate risk, remediate issues and maintain compliance – lessening the burden to your IT security team efficiently and swiftly. This is the reason why you require unified and adaptable cloud security services like Cloud Access Service Brokerage (CASB), Cloud Firewall for faster performance and consistent security policies and not to forget Cloud Native VNF application.



